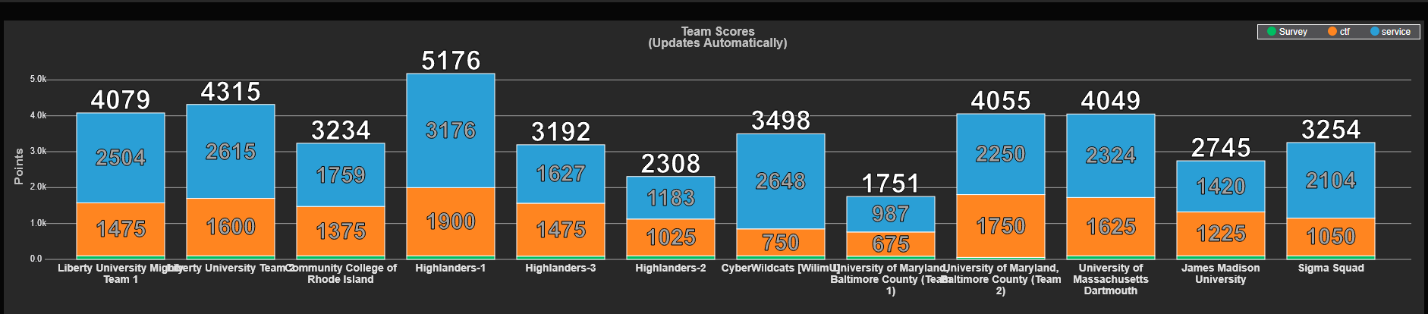
So, this was our final score, Mike said we got double our points from last year.
This was a very comprehensive competition. We got a hold of our network topology and some general goals the previous night and again 30 minutes before the competition went live.
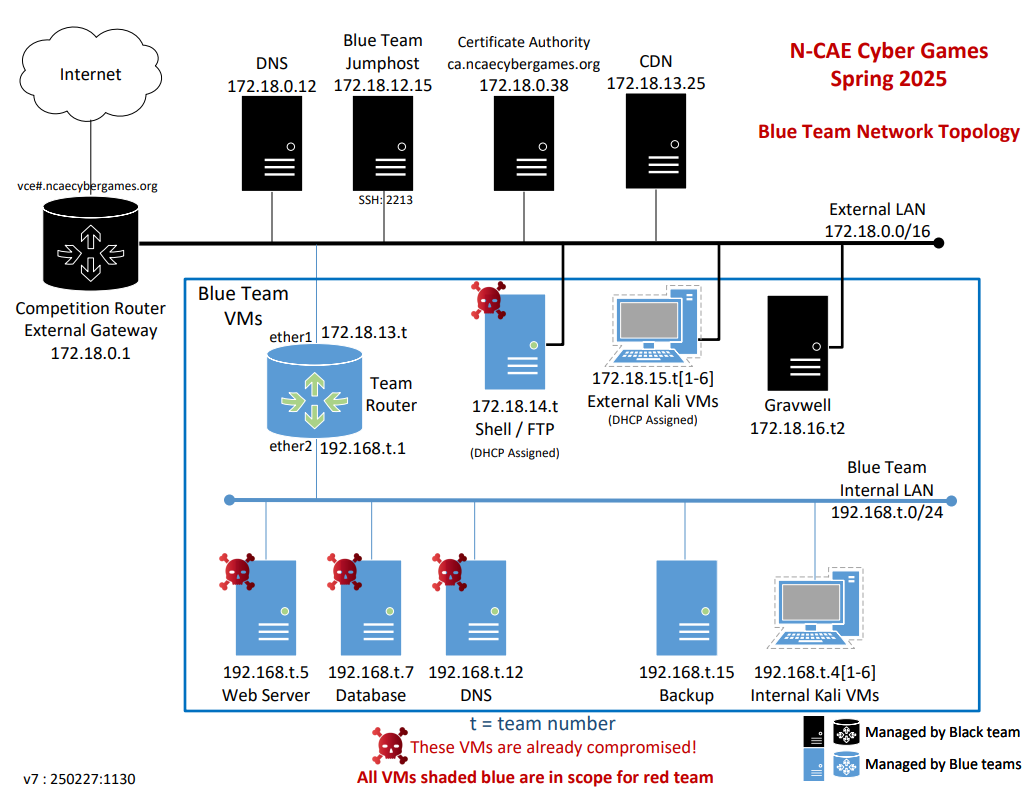
The (t) in map was our team number 3. There was also a live version from their dashboard that would update down status and goal completions.
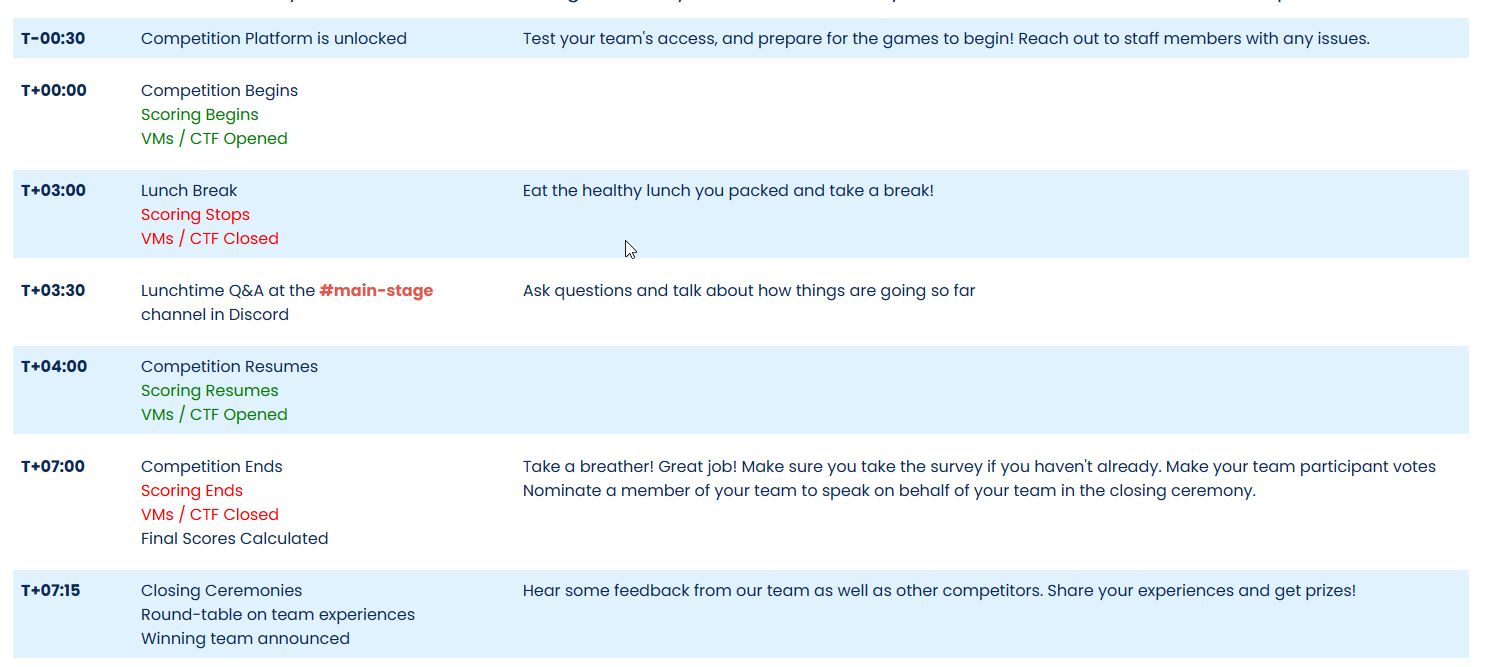
This was the schedule, which was 10am EDT for us for competition start.
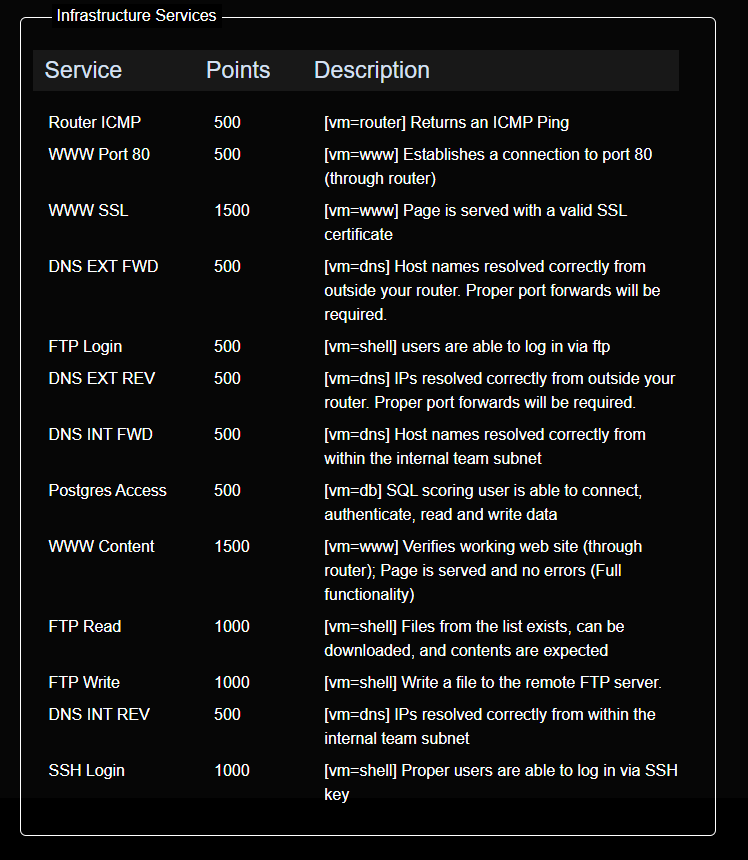
In addition to keeping the computers connected and services up, there was a drip feed of CTF challenges throughout the 6 hours that folks not working on infrastructure worked on. In these categories.
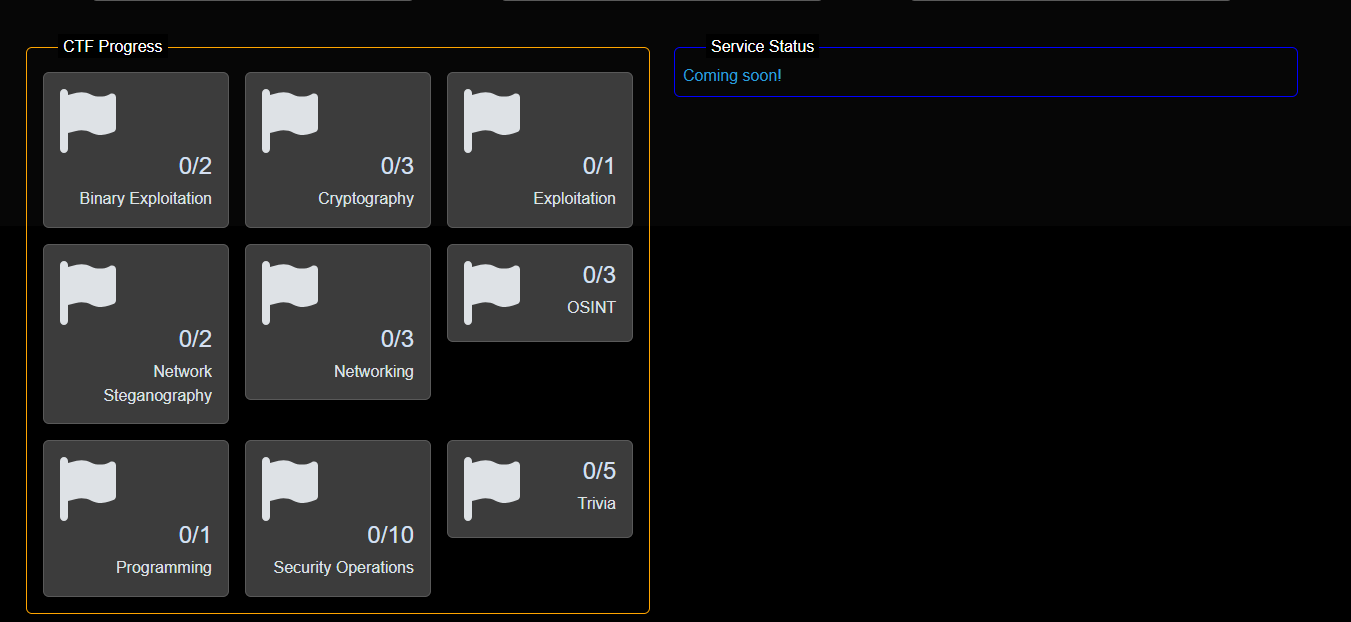
A few of them were “rabbit holes” designed to have you potentially waste a lot of time on them. Some were even required to run on one of the 3 internal kali machines.
We had a bit of a game plan going in, first was to change passwords on the not pre-compromised machines, using custom passphrases that I had up on the wall monitor. As well as starting with changing the password on the router before doing any work. After that we changed passwords to our 6 uncompromised machines, we started trying to figure out what goals we needed to accomplish on the other machines and who could best attempt to figure them out. As for myself I was manning the 2 wall monitors, with the password sheet, scoreboard and live topology map. Additionally, I took to setting up the router settings.
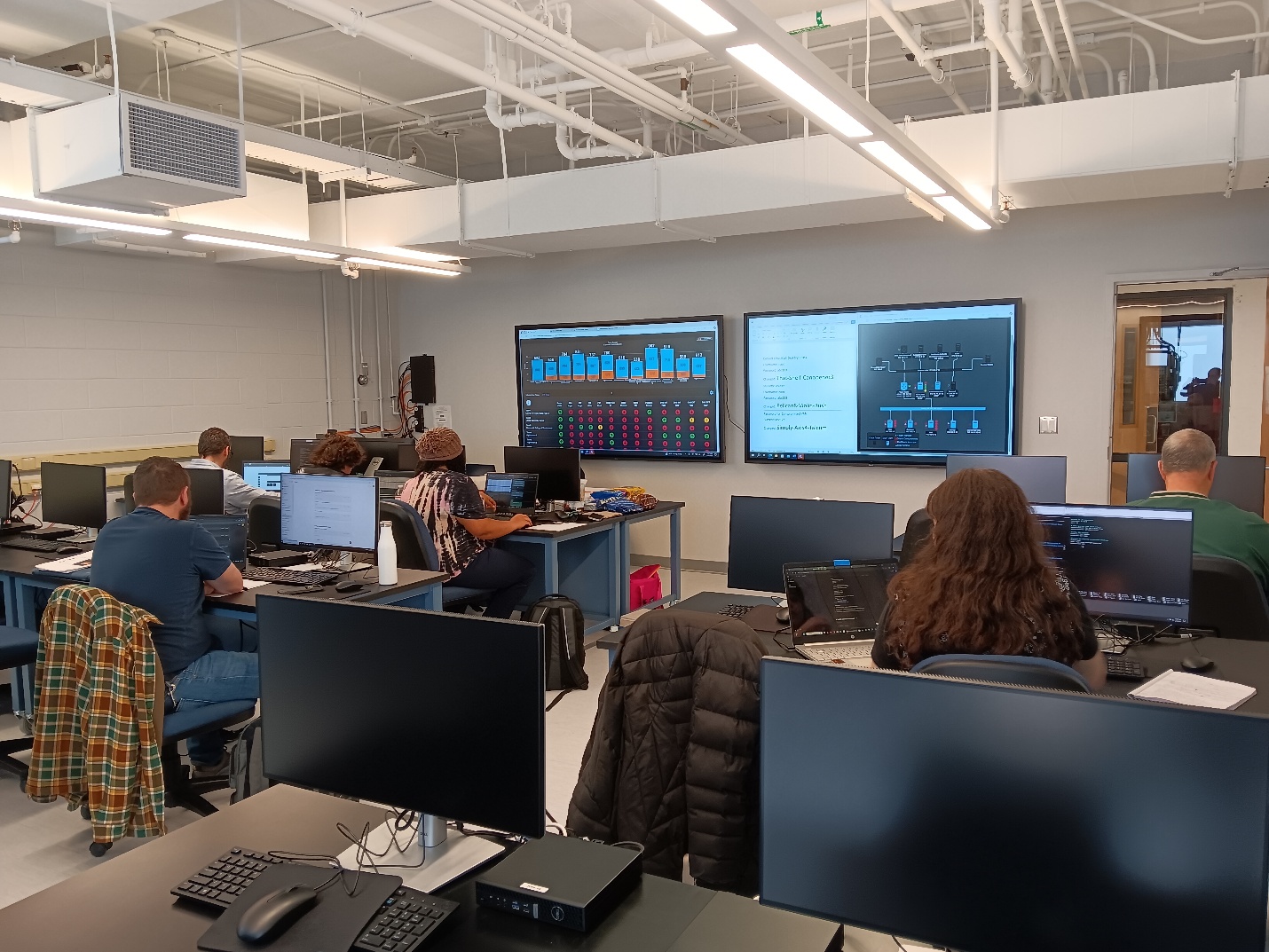
The first 3 hours were largely uneventful as far as red team interference goes, we were in the middle of the pack for the most part, gaining CTF flags and starting up services. At one point, perhaps 2 hours in, we took the lead, and Mike took a screenshot of that! However, the 5 Ubuntu machines we need to interact with were all command line interface only, as well as the router. There was a web portal for the router, but it wasn’t that helpful for me. There was not much we could do about the pre-compromised nature of the given machines; the FTP server alone had a malware on there that you had to solve a math operation every time you attempted to run a command!
The good news was, if you managed to get a service active and/or one of the goals completed, you would not lose points if red team brought it down, but you would also gain points overtime for however long it was up. There was a backup server but again you would have to know or quickly learn how to send files back and forth to it to save configuration files and what not. The webservice goal was also interconnected with the database server. You had to get the database server up and then the webserver had to host it AND get a signed SSL certificate from the external certificate signing server on the external network for full points.
After the lunch break, red team basically took everything we had aside from the router offline, I don’t believe we had anything else back up for very long after that, we made sure to get any other CTFs we could get done for additional points. Here is the archived score board, with services online at the end as well as CTF flags acquired. https://score.ne2.ncaecybergames.org/scoreboard/
After the event was over, we gathered in their main stage channel in discord and the NCAE leads talked about the event and brought up a leader for each team to speak on the experience on video or voice. Chris represented us as club president. We filled out a survey beforehand where everyone voted on a representative, an MVP and a “most improved.”
Chris got MVP from us and Maria Rodriguez earned most improved. Mike did take a group picture of all of us at the end. It was about 6pm before we all went home.
It was a very interesting but exhausting team experience but going forward I would recommend devoting twice-monthly meetings to learning the skills and techniques required for this kind of competition. For example, on our rainy day/holiday times of Wednesday at 5-6pm, devote an hour to running through sandboxes and capture the flags as a group. Those of us working on the infrastructure side of things for sure did not have any time to devote to CTF challenges so both are needed in the group. We did have full access to google and the internet at large to learn and troubleshoot, but I would push for more structure, akin to the Saturday Newport group for NCL.
-Corey Davis
